Point out-sponsored Motives: DDoS attacks tend to be waged to lead to confusion for military troops or civilian populations when political unrest or dissension turns into clear.
Raven-Storm is a strong DDoS toolkit for penetration assessments, which include assaults for various protocols prepared in python. Takedown numerous connections working with several exotic and basic protocols.
Helloện nay, ngành công nghiệp video game đã chuyển dịch cơ cấu sang loại hình on the web, từ sự phát triển thể loại MMO cho đến các dịch vụ trung gian như Steam hay Garena, thậm chí các video game offline cũng có chế độ Multiplayer để đảm bảo kết nối nhiều người chơi với nhau.
You would possibly see a counterargument that goes anything such as this: It’s not illegal to send web targeted traffic or requests over the web to your server, and so for that reason DDoS attacks, which happen to be just aggregating an overwhelming quantity of Internet targeted visitors, can't be considered against the law. This is a fundamental misunderstanding with the law, having said that.
The steps outlined above can only be realized as a result of a mix of solutions, units and persons Operating alongside one another. One example is, to mitigate Layer seven DDoS assaults it is often necessary to do the subsequent:
Though All those means are confused, balancers are loaded. Protocol attacks often contain manipulating targeted visitors at levels 3 and four in the OSI/RM (the community and transport levels, respectively). This is actually the second most typical method of DDoS assault.
You also want to have a DDoS-attack ddos web motion approach—with outlined roles and methods—so your workforce can take swift and decisive motion versus these threats.
OT: Assaults on OT require physical goods which have programming and an IP handle related to them. This could be devices which might be utilized to regulate electrical grids, pipelines, automobiles, drones or robots.
As an IT Professional, you usually takes ways to aid ready your self for the DDoS assault. Check out the subsequent capabilities and tools that will help you successfully manage an incident.
If you're able to distinguish DDoS visitors from reputable targeted visitors as explained within the earlier section, which can help mitigate the attack though holding your services a minimum of partially online: For example, if you already know the attack site visitors is coming from Eastern European sources, you may block IP addresses from that geographic region.
A protocol attack results in a support disruption by exploiting a weak spot inside the layer 3 and layer four protocol stack. A single illustration of it is a synchronized or SYN assault, which consumes all out there server sources.
The Memcached provider is actually a legit provider often utilized to aid quicken Net apps. Attackers have usually exploited Memcached implementations that are not appropriately secured, and also those that are running properly.
Alternate shipping and delivery all through a Layer seven assault: Using a CDN (content shipping and delivery community) could help assist supplemental uptime Whenever your means are combatting the attack.
This is certainly the most common form of DDoS assault and is frequently often called Layer 7 assaults, after the corresponding quantity of the applying layer within the OSI/RM.
 Edward Furlong Then & Now!
Edward Furlong Then & Now! Alfonso Ribeiro Then & Now!
Alfonso Ribeiro Then & Now! Robert Downey Jr. Then & Now!
Robert Downey Jr. Then & Now!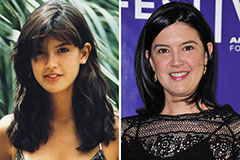 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Daryl Hannah Then & Now!
Daryl Hannah Then & Now!